Module 2: Case Studies & Examples
Steps to Follow
Download the example data here https://cyberriskmodels.com/crq-open-education
The Module 2 Assignment Excel Workbook contains several tabs, each with vulnerability data for you to analyze. To analyze the data for each tab, please follow the process below:
- Visually inspect the vulnerability data and develop a set of keywords for analysis.
- Review the auto-generated chart.
- Which vulnerabilities could likely lead to initial access?
- How many instances of this type of vulnerability are in the data set?
- Which vulnerabilities could likely lead to privilege escalation?
- How many instances of this type of vulnerability are in the data set?
- Which vulnerabilities should be recommended to be prioritized for remediation?
Example 1: Microsoft 2023 Data
The sample data is represented in the image below. Use the Microsoft 2023-tab data.
As you visually inspect the data, make a list of possible keywords. Since the data is already organized by vendor and software, you will be looking for those keywords that are related to the attack stages. What vulnerabilities might be used?
Here are some keywords relevant to this data set: denial of Service, Elevation of Privilege, Remote Code Execution, Disclosure, Cross-Site Scripting, Bypass, Spoofing, and SMB.
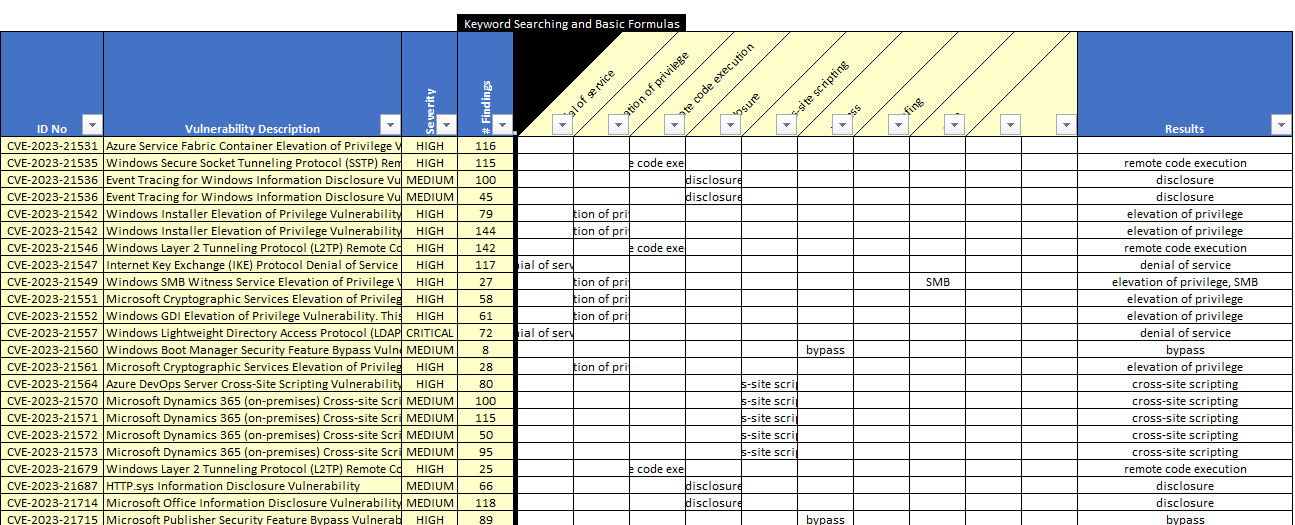
Figure 12 Microsoft 2023 Sample Data
Take note of the auto-complete charts that are included in the workbook. What do they tell you about the data? Which keywords have the highest instances?
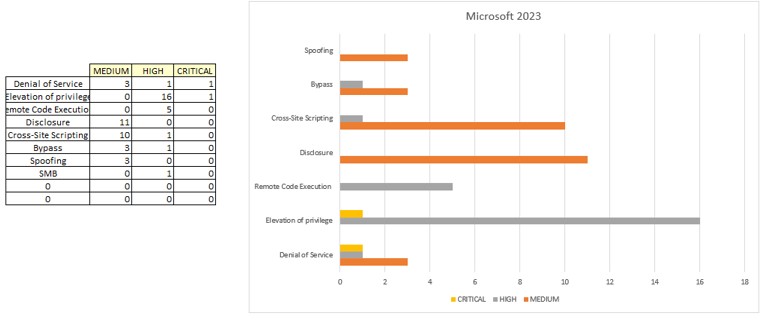
Figure 13 Microsoft 2023 Sample Data Charts
Recall how we discussed matching keywords to the first three stages of an attack. Which vulnerabilities in this data set could likely lead to initial access? If we filter on code execution and cross-site scripting, you will have a good list. How many instances of these exploitable vulnerabilities are there in the data set?
Based on this, which vulnerabilities would you recommend being prioritized for remediation?
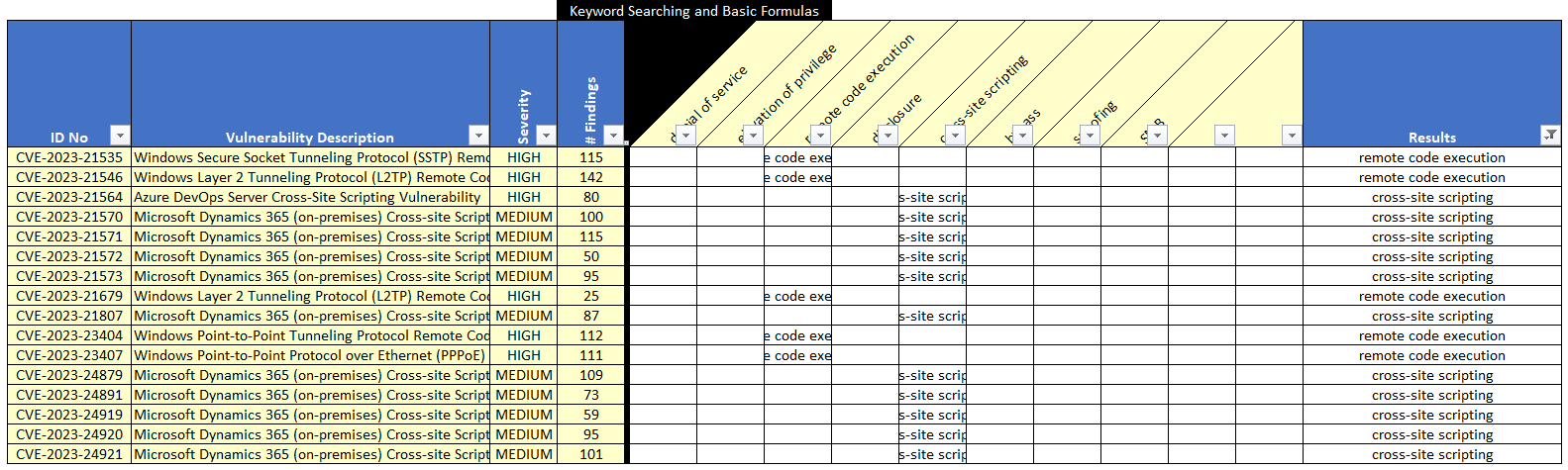
Figure 14 Microsoft Example Vulnerabilities for Initial Access
Now, can you identify the vulnerabilities most likely to be used to elevate privileges? Did you filter the list and get the same set as depicted below?
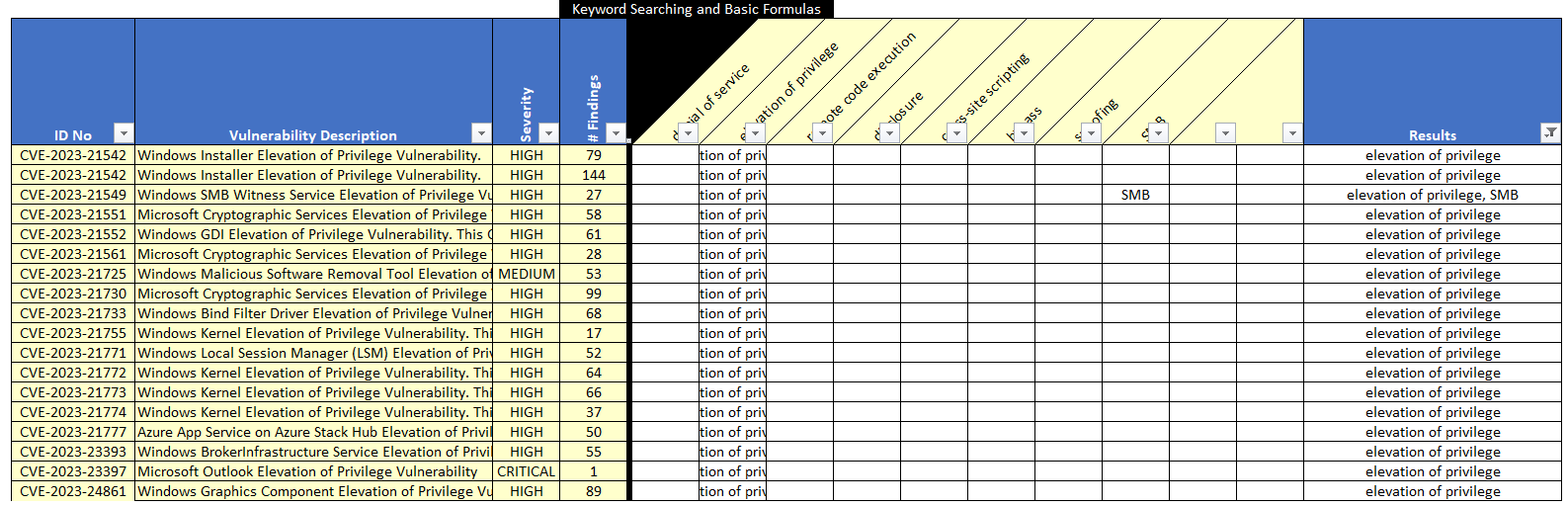
Figure 15 Microsoft Privilege Escalation Vulnerabilities
Example 2: McAfee Data
Visually inspect the data and identify operating systems. You should find Windows, Mac and Linux. Using these three keywords which operating system has more McAfee related vulnerabilities?
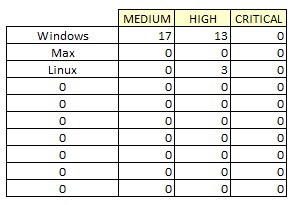
Figure 16 McAfee Operating System Findings
Now review the data and file exploitable keywords. You should have a list that includes access control, executable files, privilege escalation, cross site scripting, buffer overflow and path traversal.
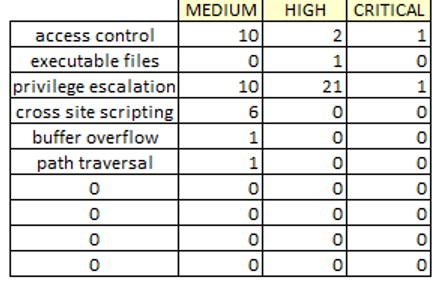
Figure 17 McAfee Exploitable Vulnerabilities
From the table above, which exploitable vulnerability has the highest count, and which has the lowest count? Now, filter the data to identify which vulnerabilities could likely lead to privilege escalation.
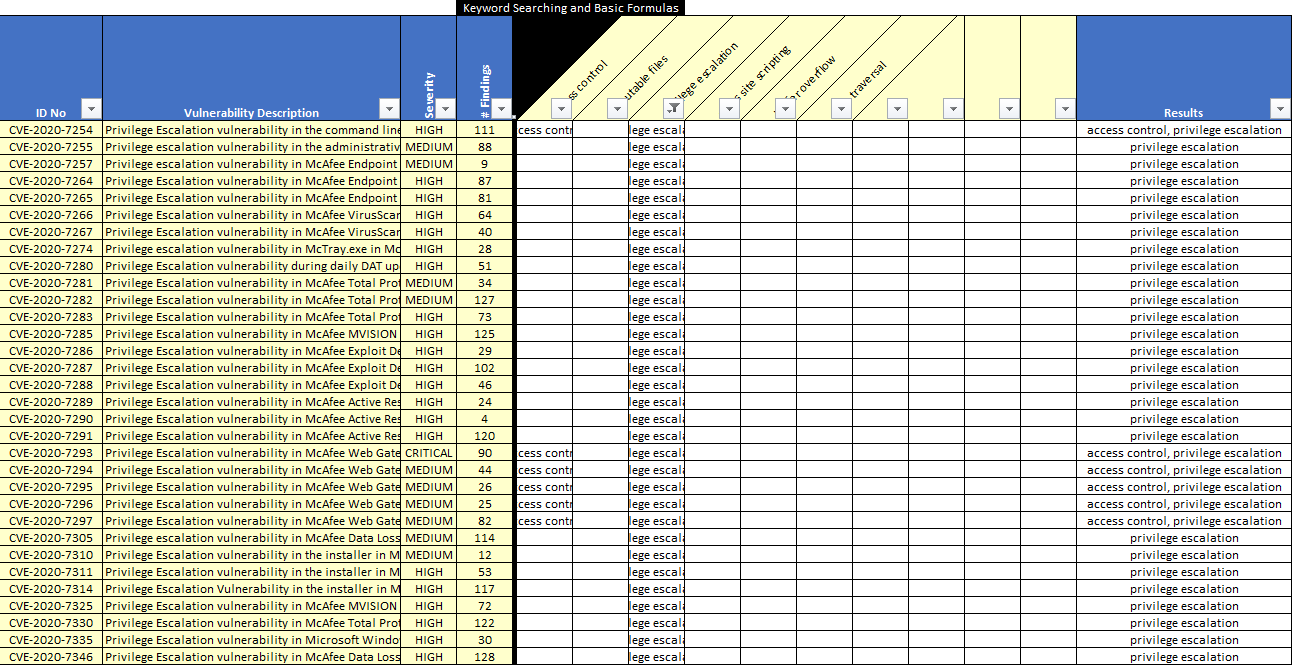
Figure 18 McAfee Privilege Escalation Vulnerabilities
Example 3: Exchange 2020 Data
Visually inspect the data and identify the keywords to use. You should have a list that includes remote code execution, elevation of privilege, cross-site scripting, authenticated, denial of service, buffer overflow, authentication bypass, brute force, disclosure, and algorithm.
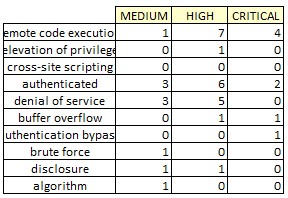
Figure 19 Exchange 2020 Keywords Charted
Which vulnerabilities are likely to lead to initial access? You can filter on remote code execution, buffer overflow, and brute force to get the list below.
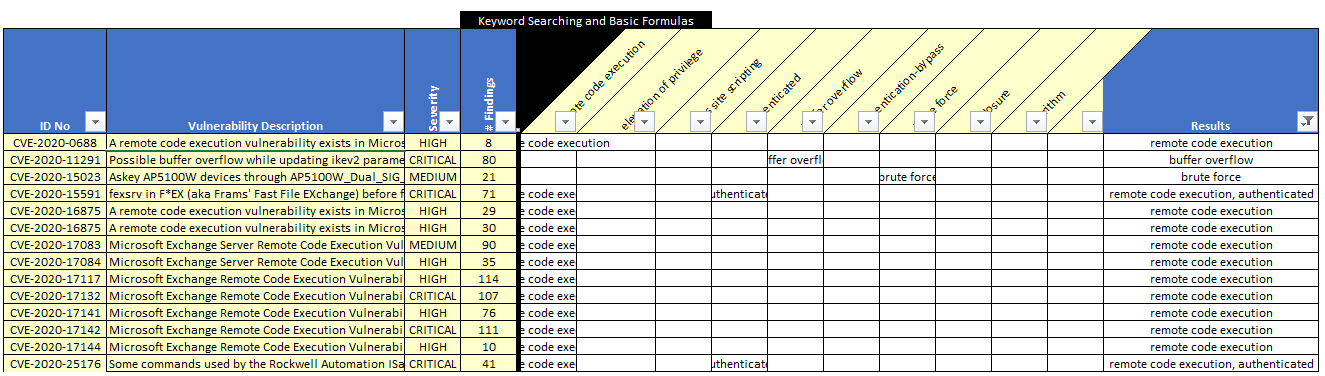
Figure 20 Exchange Data Exploitable Vulnerabilities
Which vulnerabilities could likely lead to privilege escalation?
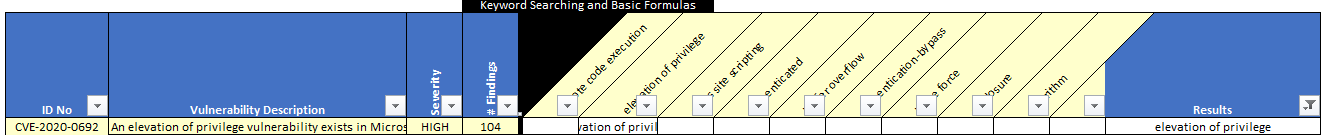
Figure 21 Exchange Privilege Escalation Vulnerability

